How to install Exchange Server 2019?
Exchange 2019 is the first version of the product that supports installation on Windows Server Core and at the deployment level this is the recommended option.
As in previous versions, this first requires preparing Active Directory for Exchange 2019. Once this activity is done, it is possible to proceed with the installation of the product.
Both the preparation process and the installation of Exchange 2019 can be done through a graphical wizard or by command line. In this sense, my preferred option is by command line, this is undoubtedly more agile than following all the windows of the wizard and as an additional advantage it works both on Windows Server with GUI ( Desktop Experience ) as well as on Windows Server Core.
In short, in this post we are going to see how to prepare the directory and install Exchange 2019 by command line ( which, as mentioned above, applies to any type of Windows installation ). I start from the basis that there is already a certain base on Exchange 2019
Software requirements for Exchange 2019:
- Windows Server 2019 Standard or Datacenter
- .Net Framework 4.8
- Visual C++ Redistributable Packages for Visual Studio 2012 Update 4
- Visual C++ Redistributable Packages for Visual Studio 2013
- IIS rule rewrite
- Additional operating system features
- UCMA 4.0 ( included in the Exchange 2019 ISO )
Prepare Active Directory for Exchange 2019
Before you prepare Active Directory for Exchange 2019, you need to confirm that the forest functional level is at Windows Server 2012 R2 or higher.
In addition, you must have the following permissions:
- Schema Admins
- Enterprise Admins
From which server to run preparation for Exchange 2019?
The server to use to run the setup in preparation mode must be associated with the Active Directory site where the domain controller with the Schema Master role is located.
Specifically from where to run the process, this could be from a domain controller or a server with Active Directory administrative tools installed, in any case it would have to be Windows Server 2019. In this sense, a server destined to be Exchange 2019 would be a good option.
How to prepare Active Directory for Exchange 2019?
As a step prior to executing the setup, it is convenient to confirm that the account we are using belongs to the groups mentioned above, for this open the cmd as administrator ( in the case of Server Core it would already be open ) and execute:
whoami-groups | findstr /I “admin”
Permissions for Active Directory preparation for Exchange 2019
With the permissions confirmed, we move forward with the installation of prerequisites. Specifically for Active Directory staging, on a non-domain controller server, you need to add the RSAT-ADDS ( Active Directory Administrative Tools ) feature. As a complement, due to a matter of dependencies and since Exchange 2019 is going to be installed later on this same server, the "Server-Media-Foundation" feature is also added and the Visual C++ packages are installed:
Install-WindowsFeature server-media-foundation,rsat-adds
Mount the ISO for Exchange 2019
To mount the Exchange 2019 ISO on Windows Server with GUI, just right click on the ISO and mount.
In Windows Server Core we are going to use the Powershell cmdlet “Mount-DiskImage”:
Mount-DiskImage file_path.iso
Setup.exe /PrepareAD /IAcceptExchangeServerLicenseTerms /OrganizationName:"organization_name"
IAcceptExchangeServerLicenseTerms_DiagnosticData Off
IAcceptExchangeServerLicenseTerms_DiagnosticData On
Keep in mind that in this case the "OrganizationName" parameter is used because there is not yet an organization in the lab environment, that is, it is an Exchange 0 installation. If, on the other hand, a forest with an existing organization is being prepared ( for example, in the case of upgrading to Exchange 2019 ), the OrganizationName parameter is not used because the organization will have already been created with a previous version of Exchange.
Note : Many of the updates for Exchange (CU) require as a previous step the preparation of the directory ( with all the permissions that this implies ). This depends solely on whether updates are included within the Cumulative Update for the directory or not. Facing an update, the preparation command is the same but in no case would it have the “OrganizationName” parameter.
In short, in this case a new Exchange organization named “ITInfs” is being created. Note that users do not interact in any way with this name, this is defined at another level.
As for the text within the analysis of the setup prerequisites, this indicates that since there are no previous versions of Exchange in the forest, it would not be possible to add Exchange 2013 or 2016 in the future, only Exchange 2019 onwards.
Installing Exchange 2019
Before starting the installation, check the prerequisites, in the case of Visual C++ 2012 and 2013 they were already installed in a previous step, it would be missing installing the .net Framework 4.8 and IIS rule rewrite.
Finally the UCMA, the additional components of Windows will be installed within the same installation process.
Install UCMA
Within the Exchange 2019 ISO, the UCMA package is included in the UCMARedist folder.
Run following the wizard options:
.\setup.exe
Shutdown -r -t 0 -f.\Setup.exe /Mode:Install /Roles:Mailbox /IAcceptExchangeServerLicenseTerms /InstallWindowsComponentsUpdate 9/30/2021 – As of CU11 , the “IAcceptExchangeServerLicenseTerms” parameter is replaced by the following options:
IAcceptExchangeServerLicenseTerms_DiagnosticData Off
IAcceptExchangeServerLicenseTerms_DiagnosticData OnNote : Be aware that exclusions must be configured in File System Antivirus for Exchange.
Open the Exchange Management Shell on Windows Server Core
On Windows Server with Desktop Experience, a folder is created that includes access to the Exchange Shell, Toolbox, and Exchange Admin Center.
In the case of Windows Server Core we have to execute the following command to open the Exchange 2019 EMS:
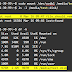
LaunchEMSFinally, try some basic cmdlets to fetch information from Exchange servers, default base, if the base is mounted, and mailboxes in the organization.
Get-ExchangeServer
Get-MailboxDatabase –Status | ft name, mounted
Get-MailboxNow you have to setup Exchnage Server URLs.
You can get script for Configure Exchange server URLs from HERE.
Script Contend:
<#
.SYNOPSIS
ConfigureExchangeURLs.ps1
.DESCRIPTION
PowerShell script to configure the Client Access server URLs
for Microsoft Exchange Server 2013/2016. All Client Access server
URLs will be set to the same namespace.
If you are using separate namespaces for each CAS service this script will
not handle that.
The script sets Outlook Anywhere to use NTLM with SSL required by default.
If you have different auth requirements for Outlook Anywhere use the optional
parameters to set those.
.PARAMETER Server
The name(s) of the server(s) you are configuring.
.PARAMETER InternalURL
The internal namespace you are using.
.PARAMETER ExternalURL
The external namespace you are using.
.PARAMETER InternalSSL
Specifies the internal SSL requirement for Outlook Anywhere. Defaults to True (SSL required).
.PARAMETER ExternalSSL
Specifies the external SSL requirement for Outlook Anywhere. Defaults to True (SSL required).
.EXAMPLE
.\ConfigureExchangeURLs.ps1 -Server sydex1 -InternalURL mail.exchangeserverpro.net -ExternalURL mail.exchangeserverpro.net
.EXAMPLE
.\ConfigureExchangeURLs.ps1 -Server sydex1,sydex2 -InternalURL mail.exchangeserverpro.net -ExternalURL mail.exchangeserverpro.net
.LINK
http://exchangeserverpro.com/powershell-script-configure-exchange-urls/
.NOTES
Written by: Paul Cunningham
Find me on:
* My Blog: https://paulcunningham.me
* Twitter: https://twitter.com/paulcunningham
* LinkedIn: https://au.linkedin.com/in/cunninghamp/
* Github: https://github.com/cunninghamp
License:
The MIT License (MIT)
Copyright (c) 2015 Paul Cunningham
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Change Log:
V1.00, 13/11/2014 - Initial version
V1.01, 26/06/2015 - Added MAPI/HTTP URL configuration
V1.02, 27/08/2015 - Improved error handling, can now specify multiple servers to configure at once.
V1.03, 09/09/2015 - ExternalURL can now be $null
V1.04, 17/11/2016 - Removed Outlook Anywhere auth settings, script now sets URLs only
V1.05, 18/11/2016 - Added AutodiscoverSCP option so it can be set to a different URL than other services
#>
#requires -version 2
[CmdletBinding()]
param(
[Parameter( Position=0,Mandatory=$true)]
[string[]]$Server,
[Parameter( Mandatory=$true)]
[string]$InternalURL,
[Parameter( Mandatory=$true)]
[AllowEmptyString()]
[string]$ExternalURL,
[Parameter( Mandatory=$false)]
[string]$AutodiscoverSCP,
[Parameter( Mandatory=$false)]
[Boolean]$InternalSSL=$true,
[Parameter( Mandatory=$false)]
[Boolean]$ExternalSSL=$true
)
#...................................
# Script
#...................................
Begin {
#Add Exchange snapin if not already loaded in the PowerShell session
if (Test-Path $env:ExchangeInstallPath\bin\RemoteExchange.ps1)
{
.$env:ExchangeInstallPath\bin\RemoteExchange.ps1
Connect-ExchangeServer -auto -AllowClobber
}
else
{
Write-Warning "Exchange Server management tools are not installed on this computer."
EXIT
}
}
Process {
foreach ($i in $server)
{
if ((Get-ExchangeServer $i -ErrorAction SilentlyContinue).IsClientAccessServer)
{
Write-Host "----------------------------------------"
Write-Host " Configuring $i"
Write-Host "----------------------------------------`r`n"
Write-Host "Values:"
Write-Host " - Internal URL: $InternalURL"
Write-Host " - External URL: $ExternalURL"
Write-Host " - Outlook Anywhere internal SSL required: $InternalSSL"
Write-Host " - Outlook Anywhere external SSL required: $ExternalSSL"
Write-Host "`r`n"
Write-Host "Configuring Outlook Anywhere URLs"
$OutlookAnywhere = Get-OutlookAnywhere -Server $i
$OutlookAnywhere | Set-OutlookAnywhere -ExternalHostname $externalurl -InternalHostname $internalurl `
-ExternalClientsRequireSsl $ExternalSSL -InternalClientsRequireSsl $InternalSSL `
-ExternalClientAuthenticationMethod $OutlookAnywhere.ExternalClientAuthenticationMethod
if ($externalurl -eq "")
{
Write-Host "Configuring Outlook Web App URLs"
Get-OwaVirtualDirectory -Server $i | Set-OwaVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/owa
Write-Host "Configuring Exchange Control Panel URLs"
Get-EcpVirtualDirectory -Server $i | Set-EcpVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/ecp
Write-Host "Configuring ActiveSync URLs"
Get-ActiveSyncVirtualDirectory -Server $i | Set-ActiveSyncVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/Microsoft-Server-ActiveSync
Write-Host "Configuring Exchange Web Services URLs"
Get-WebServicesVirtualDirectory -Server $i | Set-WebServicesVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/EWS/Exchange.asmx
Write-Host "Configuring Offline Address Book URLs"
Get-OabVirtualDirectory -Server $i | Set-OabVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/OAB
Write-Host "Configuring MAPI/HTTP URLs"
Get-MapiVirtualDirectory -Server $i | Set-MapiVirtualDirectory -ExternalUrl $null -InternalUrl https://$internalurl/mapi
}
else
{
Write-Host "Configuring Outlook Web App URLs"
Get-OwaVirtualDirectory -Server $i | Set-OwaVirtualDirectory -ExternalUrl https://$externalurl/owa -InternalUrl https://$internalurl/owa
Write-Host "Configuring Exchange Control Panel URLs"
Get-EcpVirtualDirectory -Server $i | Set-EcpVirtualDirectory -ExternalUrl https://$externalurl/ecp -InternalUrl https://$internalurl/ecp
Write-Host "Configuring ActiveSync URLs"
Get-ActiveSyncVirtualDirectory -Server $i | Set-ActiveSyncVirtualDirectory -ExternalUrl https://$externalurl/Microsoft-Server-ActiveSync -InternalUrl https://$internalurl/Microsoft-Server-ActiveSync
Write-Host "Configuring Exchange Web Services URLs"
Get-WebServicesVirtualDirectory -Server $i | Set-WebServicesVirtualDirectory -ExternalUrl https://$externalurl/EWS/Exchange.asmx -InternalUrl https://$internalurl/EWS/Exchange.asmx
Write-Host "Configuring Offline Address Book URLs"
Get-OabVirtualDirectory -Server $i | Set-OabVirtualDirectory -ExternalUrl https://$externalurl/OAB -InternalUrl https://$internalurl/OAB
Write-Host "Configuring MAPI/HTTP URLs"
Get-MapiVirtualDirectory -Server $i | Set-MapiVirtualDirectory -ExternalUrl https://$externalurl/mapi -InternalUrl https://$internalurl/mapi
}
Write-Host "Configuring Autodiscover"
if ($AutodiscoverSCP) {
Get-ClientAccessServer $i | Set-ClientAccessServer -AutoDiscoverServiceInternalUri https://$AutodiscoverSCP/Autodiscover/Autodiscover.xml
}
else {
Get-ClientAccessServer $i | Set-ClientAccessServer -AutoDiscoverServiceInternalUri https://$internalurl/Autodiscover/Autodiscover.xml
}
Write-Host "`r`n"
}
else
{
Write-Host -ForegroundColor Yellow "$i is not a Client Access server."
}
}
}
End {
Write-Host "Finished processing all servers specified. Consider running Get-CASHealthCheck.ps1 to test your Client Access namespace and SSL configuration."
Write-Host "Refer to http://exchangeserverpro.com/testing-exchange-server-2013-client-access-server-health-with-powershell/ for more details."
}
#...................................
# Finished
#...................................

















Post a Comment