Install OpenVPN on Centos 8
OpenVPN is virtual private network (VPN) software installed on a virtual private server (VPS). VPNS Take advantage of the network provided by the VPS without the need to connect through an SSH or RDP session. You can connect devices to the VPN server and use that network to mask your local area network.
OpenVPN Requirements
You will need root or administrator access to a server. You can install OpenVPN on a Linux, Windows VPS, or a dedicated server. Below are the steps to install OpenVPN. Note that you will need to use a command line interface to do this.
OpenVPN Preparation
Step 1: Update your system.
Sudo yum update
Step 2: Edit the SELinux Config File
nano /etc/selinux/config
Step 3: Set Selinux to disabled
SELINUX=disabled
- ctrl + x
- Press the key and
- Press the ENTER key
Step 4: Edit the SYSCTL.CONF file
nano /etc/sysctl.conf
Step 5: Add the following line to the SYSCTL.CONF file to enable IP Forwarding
net.ipv4.ip\_forward = 1
- ctrl + x
- Press the key and
- Press the ENTER key
sysctl -pdnf install epel-release -ydnf install openvpn -ycd /etc/openvpnwget https://github.com/OpenVPN/easy-rsa/releases/download/v3.0.6/EasyRSA-unix-v3.0.6.tgztar -xvzf EasyRSA-unix-v3.0.6.tgzmv EasyRSA-v3.0.6 easy-rsacd /etc/openvpn/easy-rsanano varsset_var EASYRSA "$PWD"set_var EASYRSA_PKI "$EASYRSA/pki"set_var EASYRSA_DN "cn_only"set_var EASYRSA_REQ_COUNTRY "USA"set_var EASYRSA_REQ_PROVINCE "Seatle"set_var EASYRSA_REQ_CITY "Seatle"set_var EASYRSA_REQ_ORG "<HOSTNAME> CERTIFICATE AUTHORITY"set_var EASYRSA_REQ_EMAIL "<yourEmail@itinfs.com>"set_var EASYRSA_REQ_OU "<HOSTNAME> EASY CA"set_var EASYRSA_KEY_SIZE 2048set_var EASYRSA_ALGO rsaset_var EASYRSA_CA_EXPIRE 7500set_var EASYRSA_CERT_EXPIRE 365set_var EASYRSA_NS_SUPPORT "no"set_var EASYRSA_NS_COMMENT "<HOSTNAME> CERTIFICATE AUTHORITY"set_var EASYRSA_EXT_DIR "$EASYRSA/x509-types"set_var EASYRSA_SSL_CONF "$EASYRSA/openssl-easyrsa.cnf"set_var EASYRSA_DIGEST "sha256"./easyrsa init-pki./easyrsa build-ca./easyrsa gen-req <HOSTNAME> nopass./easyrsa sign-req server <HOSTNAME>openssl verify -CAfile pki/ca.crt pki/issued/<HOSTNAME>.crtpki/issued/<HOSTNAME>.crt: OK./easyrsa gen-dhcp pki/ca.crt /etc/openvpn/server/cp pki/dh.pem /etc/openvpn/server/cp pki/private/<HOSTNAME>.key /etc/openvpn/server/cp pki/issued/<HOSTNAME>.crt /etc/openvpn/server/./easyrsa gen-req client nopass./easyrsa sign-req client clientcp pki/ca.crt /etc/openvpn/client/cp pki/issued/client.crt /etc/openvpn/client/cp pki/private/client.key /etc/openvpn/client/nano /etc/openvpn/server/server.confport 1194proto udpdev tunca /etc/openvpn/server/ca.crtcert /etc/openvpn/server/<HOSTNAME>.crtkey /etc/openvpn/server/<HOSTNAME>.keydh /etc/openvpn/server/dh.pemserver 10.8.0.0 255.255.255.0push "redirect-gateway def1"
push "dhcp-option DNS 208.67.222.222"push "dhcp-option DNS 208.67.220.220"duplicate-cncipher AES-256-CBCtls-version-min 1.2tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256auth SHA512auth-nocachekeepalive 20 60persist-keypersist-tuncompress lz4daemonuser nobodygroup nobodylog-append /var/log/openvpn.logverb 3- ctrl + x
- Press the key and
- Press the ENTER key
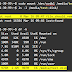
systemctl start openvpn-server@serversystemctl enable openvpn-server@serversystemctl status openvpn-server@servernano /etc/openvpn/client/client.ovpnclientdev tunproto udpremote <Server IP> 1194ca ca.crtcert client.crtkey client.keycipher AES-256-CBCauth SHA512auth-nocachetls-version-min 1.2tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256resolv-retry infinitecompress lz4nobindpersist-keypersist-tunmute-replay-warningsverb 3- ctrl + x
- Press the key and
- Press the ENTER key
firewall-cmd --permanent --add-service=openvpnfirewall-cmd --permanent --zone=trusted --add-service=openvpnfirewall-cmd --permanent --zone=trusted --add-interface=tun0firewall-cmd --add-masqueradefirewall-cmd --permanent --add-masquerade<HOSTNAME>ovpn=$(ip route get 8.8.8.8 | awk 'NR==1 {print $(NF-2)}')firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.0.0/24 -o $hqsrv702659ovpn -j MASQUERADEfirewall-cmd --reloadscp -r root@**\<SERVER IP>**:/etc/openvpn/client .













Post a Comment